Managing secrets and environment variables
Learn how to securely handle secrets like API keys in Node.js using environment variables and the dotenv module.
Lets Go!

Managing secrets and environment variables
Lesson 45
Learn how to manage API keys, database credentials, and other sensitive information securely using environment variables.
Get Started 🍁Introduction to Handling Secrets in Node.js
Welcome to our course on handling secrets in Node.js! My name is Ben, and I will be your guide as we explore the best practices for managing sensitive information like API keys in your code.
In this course, we will delve into the dangers of storing secrets directly in your code and the potential risks of leaking them, especially when using version control. We will learn how to effectively use environment variables to securely store and access our secrets without compromising our application's security.
Have you ever wondered how you can protect your API keys in Node.js applications? Join us as we uncover the secrets to keeping your sensitive information safe and sound. Are you ready to level up your security game? Let's dive in!
Main Concepts of Handling Secrets with Node.js
-
Storing Secrets in Code
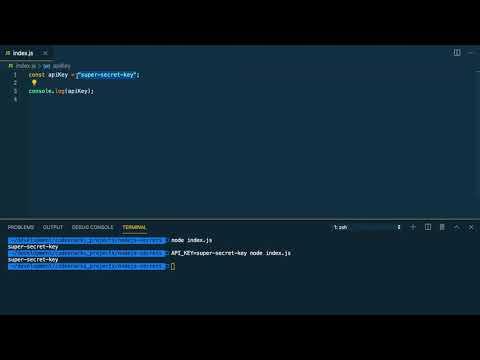
- Initially, secrets like API keys are often stored directly in the code, such as in an index.js file. However, this method is not secure as the secret could be easily leaked, especially if the code is shared in version control.
-
Using Environment Variables
- An alternative method is to use environment variables. By setting the API key as an environment variable, for example,
api_key=super_secret_key node index.js, you can access it within your Node.js application using theprocess.envproperty.
- An alternative method is to use environment variables. By setting the API key as an environment variable, for example,
-
Adding Environment Variables to Package.json
- To avoid writing the environment variable command each time the application is started, you can add it to the
scriptssection of thepackage.jsonfile. This allows you to start the application usingnpm start.
- To avoid writing the environment variable command each time the application is started, you can add it to the
-
Using
dotenvModule- To prevent the API key from being committed to the repository along with the
package.json, thedotenvmodule can be used. This module loads variables from a.envfile intoprocess.env, helping keep sensitive information secure.
- To prevent the API key from being committed to the repository along with the
-
Excluding
.envFile from Version Control- To further enhance security, the
.envfile should be excluded from version control by adding it to the.gitignorefile. This ensures that secrets are kept in a separate, secure location and not accidentally exposed.
- To further enhance security, the
Practical Applications of Managing Secrets in Node.js
Handling secrets like an API key in Node.js requires careful consideration to ensure security. Here's a step-by-step guide on how to securely manage secrets using environment variables and the dotenv module:
-
Avoid Hardcoding Secrets in Code:
- Never hardcode sensitive information like API keys directly into your code.
-
Utilize Environment Variables:
- Start your Node.js application with environment variables by prepending them before your usual command.
api_key=super_secret_key node index.js
- Start your Node.js application with environment variables by prepending them before your usual command.
-
Accessing Environment Variables in Node.js:
- You can access these environment variables using the
process.envobject in your Node.js application.
- You can access these environment variables using the
-
Simplify Starting the Application:
- Add a start script in your
package.jsonto easily start your application without typing the environment variable each time."scripts": { "start": "node index.js" }
- Add a start script in your
-
Using
dotenvfor Secure Management:- Install the
dotenvmodule to load variables from a.envfile intoprocess.env.npm install dotenv
- Install the
-
Create a
.envFile:- Create a
.envfile and add your API key.API_KEY=super_secret_key
- Create a
-
Load Environment Variables with
dotenv- Require
dotenvin yourindex.jsfile to load environment variables.require('dotenv').config();
- Require
-
Securely Store
.envFile:- Exclude the
.envfile from version control by adding it to a.gitignorefile..env
- Exclude the
By following these steps, you can securely manage secrets in your Node.js applications and avoid accidentally exposing sensitive information. Give it a try by creating your own .env file and accessing the API key in your Node.js application!
Test your Knowledge
What package is commonly used to manage environment variables in Node.js?
Advanced Insights into Securing Secrets in Node.js
Securing sensitive information like API keys is crucial in application development. While it may seem easy to just store them directly in your code, this poses a significant security risk, especially if the code is shared or in version control.
Leveraging Environment Variables
A better approach is to use environment variables to store and access your secrets. By setting environment variables before starting your Node.js application, you can keep your secrets separate from your codebase. This can be achieved by prepending the start command with the variable assignment:
api_key=super_secret_key node index.js
Managing Secrets with dotenv
To simplify this process and keep your secrets even more secure, you can utilize the dotenv module. This module allows you to load variables from a .env file into your application's environment. By installing dotenv and creating a .env file to store your secrets, you can easily access them in your code without exposing them.
require('dotenv').config(); const apiKey = process.env.API_KEY;
Best Practices for Secret Management
To prevent accidentally exposing your secrets, it's essential to exclude the .env file from version control. This can be achieved by adding it to your .gitignore file to ensure it remains private and secure.
By following these practices, you can enhance the security of your Node.js applications and protect sensitive information from unauthorized access. Remember, security is a continuous process, so always be vigilant and stay updated on the latest best practices.
Curiosity Question
How can you further enhance the security of your application by implementing additional layers of protection for your secrets?
Additional Resources for Handling Secrets in Node.js
- Article: Best Practices for Handling API Keys in Node.js
- Blog Post: Securely Managing Environment Variables in Node.js
- GitHub Repository: dotenv - Loads environment variables from a .env file
- Documentation: Node.js process object
Explore these resources to deepen your understanding of securely managing secrets in your Node.js applications. Enhance your knowledge and improve your coding practices for a more secure development environment. Happy coding!🚀
Practice
Task: Use the dotenv package to load environment variables from a .env file and access them in your Node.js app.
